Summary ->> CONTEMPLATION ->> Closing
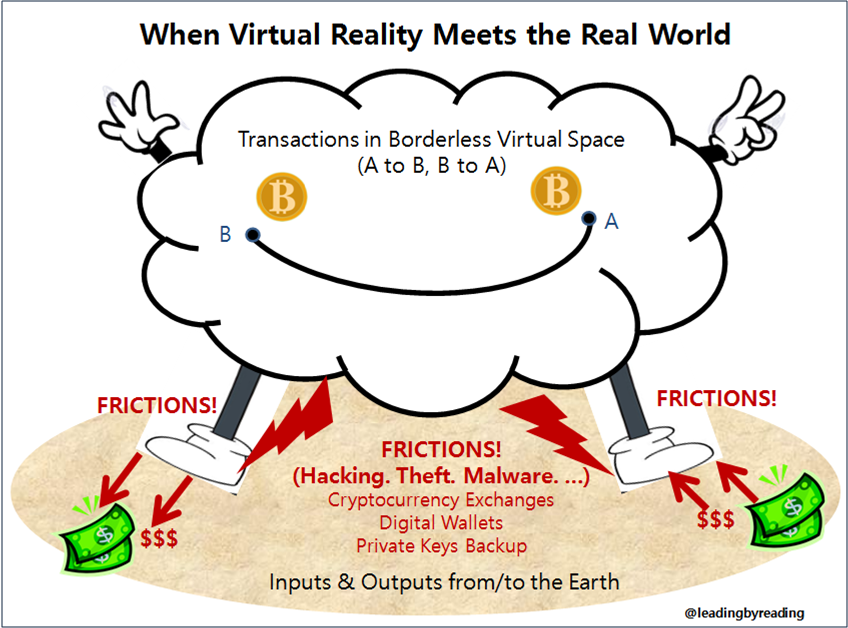
FRICTIONS IN THE REAL WORLD
Even if Bitcoin itself is difficult to hack, there does exist potential for security risks at various stages of the transaction process. 98
Bitcoins are held in wallets and traded through digital currency exchanges. There are various security risks inherent in each of these two components. 99
Digital Wallets
- To pay a recipient for goods or services in bitcoin, you first need a bitcoin wallet because the blockchain only records transactions, it doesn’t tabulate how many bitcoins are owned by an address. 100
- The wallet can be stored on your computer, on your phone, on the Web, or in a dedicated bitcoin hardware device. 101
- Wallets can be compromised, manipulated, stolen and transferred, just like any other store of value on a computer. 102
- Bitcoin wallets lack good private key security. People often forget their protective PIN/passwords, or lose the hard drive where the store is located, and often that means the value store is forever inaccessible. 103 √
- There are two types of wallets. The types of wallets you will need will vary based on what you planned to do with your cryptocurrencies, like trading more frequently or holding long-term. 104
- Online web wallets or mobile wallets are categorized as Hot Storage Wallets. 105
- Hot wallets are ones that are easily connected to the internet, and therefore accessible through the internet anywhere (although, they are not always connected to the internet). They are much more susceptible to attacks and hackers because of this and the wallet being stored somewhere online. 106 √
- Cold storage wallets, which are not connected to the internet, would be better for the purpose of storing cryptocurrencies for long term purposes. 107
- Most experts recommend keeping your value in an offline wallet (i.e. Cold Storage Wallet) that can’t be accessed by malware or hackers. However, this can also make it harder to use that value. The offline nature can add “days of waiting” to use or update the value store. 108 This can be a drawback in case users need to withdraw the value immediately when market price of Bitcoin (or other cryptocurrencies) plummets.
Cryptocurrency Exchanges
- It was reported the reason cryptocurrency exchanges were hacked was because, to maintain required liquidity, they kept values in hot wallets which are prone to attacks. √
- Cryptocurrency exchanges are targets of hackers. The Coinbase is claimed to be the safest exchange, but the public may not know whether they are actually compromised or not. 109
- Developers are always improving wallet security, but there are also those looking to access other peoples’ wallets illegally to swipe their tokens and coins. 110 √
- In the transaction process, two-factor identification is commonly used as a security measure. Having the security of a transaction linked to an email address or a cell phone number means that anyone with access to those components can authenticate transactions. If a hacker is able to determine some of your non-cryptocurrency-related personal information, s/he may be able to infiltrate your transactions in that space regardless. 111 √
- Part of the issues of widely publicized frauds, scams, and hacks which have plagued individual investors and even major cryptocurrency exchanges, is simply that the technology and the space itself are new. 112
- While this newness makes cryptocurrencies like Bitcoin potentially very profitable in terms of investment, it also means that there are those looking to capitalize on security holes before they are corrected. 113 √
__________
- Coinbase – the biggest cryptocurrency exchange – argues that, though there have been Bitcoin-related compromises in the past, this does not reflect upon the security of the Bitcoin network itself. Bitcoin-related thefts are usually the result of improper security or negligence on the part of the person or service holding the bitcoins. 114 √
- It is estimated that, Coinbase alone, the global market’s largest bitcoin brokerage and wallet platform, serves more than 13 million active users as of 2017. 115
Private Key Security
- At the margin, coins stored in lost wallets or sent to addresses whose owners have lost their private keys are not recoverable. 116
- There are private third-party firms that provide private key storage services offline. For example, a digital-coin vault is maintained by the firm Xapo, 200 meters belowground in Switzerland. Cryptocurrency “keys” are kept there on servers that have never touched the Internet. 117
- The ultimate irony is that the gold standard in security, storing private keys in what’s known as “cold storage,” without connection to the Internet, often means putting them in the very places blockchain advocates hoped to avoid: banks. For instance, one cryptocurrency hedge fund manager once went to check on his safe-deposit box at Wells Fargo, which stored the key to $5 million, only to find the drawer empty. 118
- One article rated the best digital wallets for 2018: The second rank is ‘Ledger or Trezor,’ which provide hardware wallets and the top rank is ‘Paper wallet’ or ‘other cold storage.’ 119 √
- Paper wallet is simply a document that contains all the information you need to generate the bitcoin private keys you need. It often takes the form of a piece of paper with a QR code that can be scanned into a software wallet when you so desire. By storing your bitcoin offline, trusting nothing and no one but yourself, and you have all the information you need to control and access your bitcoin, you’re using the strongest “cold storage” method out there. 120 √
- Which indicates an ultimate irony: In keeping safe backups of their private keys, the new technology is no better or worse than current backup system in traditional banking. √
- As the authors stated, “With greater freedom – better privacy, stronger security, and autonomy from third party cost structures and system failures – comes greater responsibility (of keeping your private key, which is a combination of alphanumeric code in more than twenty digits).” Otherwise, we might as well stuff our mattress with cash. 121 √
___________
- On the flip side, this also indicates a greater need for improvement in these areas for seamless real world application of the new technology moving forward.
(4) SUMMING UP: MEETING SEVEN CONDITIONS AS PRE-REQUISITES?
As readers may have noticed from various facets and dynamics I have elaborated so far, the bitcoin technology at this stage contains several potential risks, hence creating uncertainty.
However, what matters is not the limitations but how to move forward from here. The good news is, new technological developments within the network community can make a break-through giving birth to a powerful application, under effective leadership after all. Bad news can be, if this is a much slower process without effective leadership, we may see other powerful players emerging as killer apps that will find mass adoption, leaving the bitcoin blockchain as a small niche player eventually. 122
Below is a summary table for our lengthy discussions.

(End of Part 7 out of 9. To be continued in the next article)

